Hackback 0x01: You Gonna Finish That?
Prelude
There’s been debate about the whole concept of hacking back and whether or not someone should only defend themselves and their assets, or apply the “Offense is the best form of defense” concept to these situations. Personally I lean towards striking back, but only under certain circumstances such as:
You’ve been under constant attack from a group/person.
You’ve already taken all the recommended procedures to prevent further attacks.
You’ve notified a single or multiple parties that have the ability to halt the attacks you’ve been under. (eg: Notifying No-IP that one of their dynamic DNS users has been using their services as a part of their campaign.) to no avail.
Lucky for you, this is a tale where back in 2019 the stars have aligned in favor of a hackback after an attack on me was repeated, and all my warnings and abuse mails have fallen on deaf ears. so buckle up.

Disclaimer: Some URLS, Screenshots and some otherwise potentially identifying details have been altered.
Chapter 0x01: The Attack
Twas a somewhat fine morning that was only interrupted by my phone’s notification tone that hasn’t been changed in quite some time now (i’m open for suggestions), it was an email telling me that my hosting subscription was almost up and that I needed to log in using the "provided link" in order to update my payment. Given the Nigerian-prince-esque nature of the email and its formatting, I spun up a sandboxed environment, threw the link inside and took a walk inside the source code. Many of you already know that this part usually ends in something like this:
So I did what any responsible security researcher did and moved the email to the spam folder decided to visit the fake site and explore a little bit.
What I tend to notice a lot when analyzing/exploring those low quality phishing campaigns is that unless they’re a part of a spear phishing campaign aimed at a specific organization or person as a part of an actual attack or a red team engagement, they’re often built hastily, carelessly, and usually while having some “how to hack accounts 2019” tutorial open in the next tab.
Fun Fact: After sending a message to everyone to not open any links in the email, I had a colleague at my desk talking about a "weird email" that they got and how that even though they have provided their credentials, they couldn't get to a payment page to renew their hosting subscription. Yeah..
Chapter 0x02: Poking Around the Enemy
Starting my endeavor, I opened up a couple of terminal tabs, in the first one I fed nmap the domain in question along with some arguments that reflect how much I want to get to know it.
Mind you, I was in a hurry, and i was willing to bet money that that person/group didn’t have any sort of defenses/prevention/detection systems in place.
In the next tab, my dear dirsearch ran a quick little directory brute forcing.
After some manual searching about, and browsing the site itself, I kept checking in every once in a while on my terminal tabs, waiting for any of them to hatch something of interest.
Time to celebrate?
Chapter 0x03: "Exploitation" (In quotes)
This is exploitation as much as walking into a house with an open door is breaking and entering. (is it?) As my mind was racing with multiple scenarios of how I can get inside that phpmyadmin panel, Brute force? CVE-2009-1151? or maybe i ca-
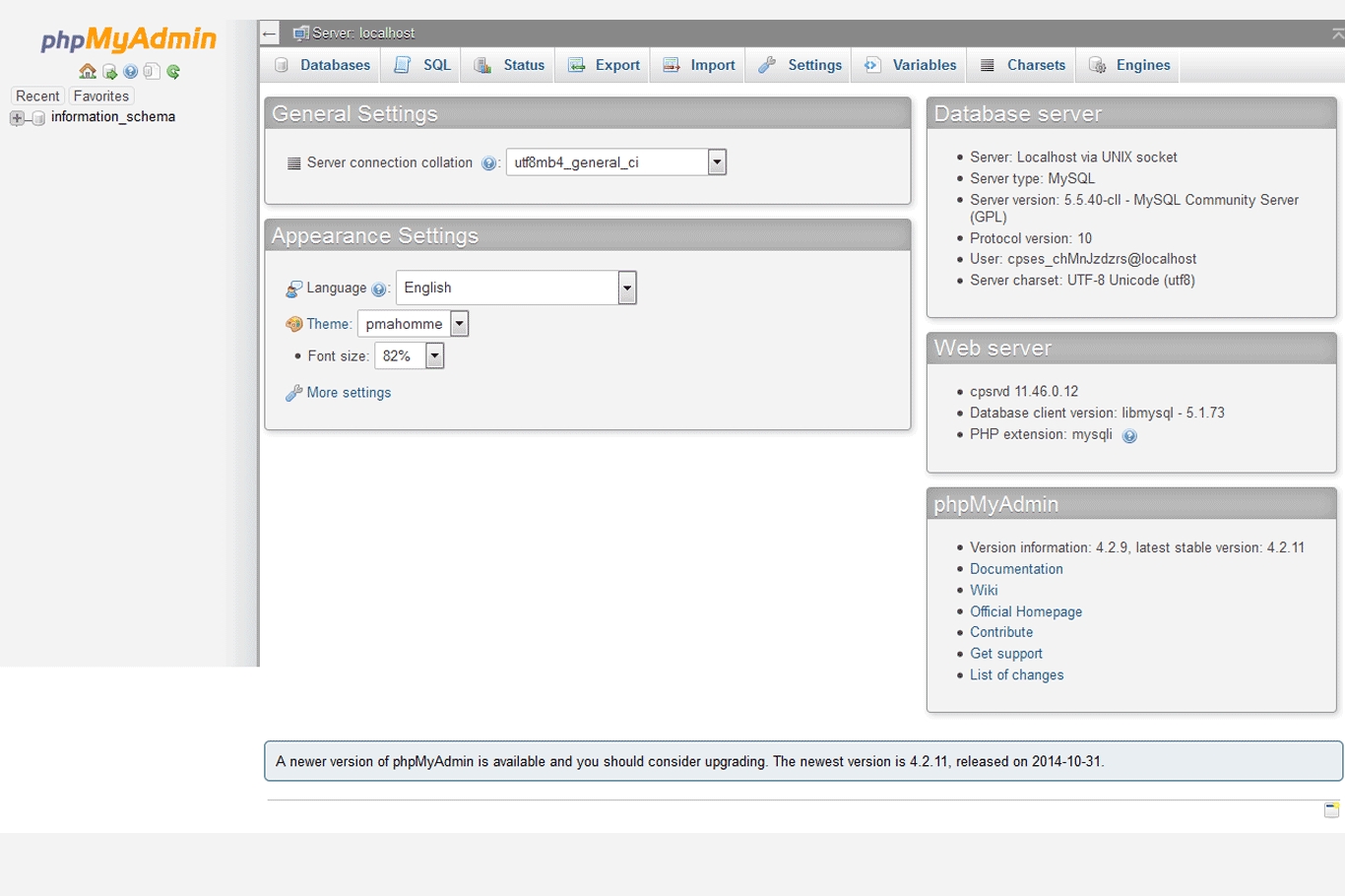
No authentication. and umm… yeah that concludes our “exploitation” phase.
Chapter 0x04: SELECT `shell` from `shells`;--
To my disappointment, the treasure box was filled with cobweb and information_schemas. Looking over the server information, I found that this MySQL server instance was installed and turned on as a part of a default XAMPP installation on windows (told you.) But all is not lost! a machine can still be very easily owned through an open phpmyadmin panel, even if it was sitting there collecting dust. One might think about using one of phpmyadmin’s authenticated code execution exploits/metasploit modules, but that will only work if the stars are aligned, which in this case means the service version, server environment, and in some cases, memory alignment all blow in your favor. But why go down that rabbit hole where we have a perfectly stable solution staring right at us?
Side stage, SQL file operations make an entrance.
Gaining remote code execution using a SQL shell is easy as long as you have the ingredients, which goes something like:
Since the SQL shell will diligently SELECT anything we tell it to, all you have to do is to SELECT anything between quotes. ie:
Pair that with the fact that MYSQL can write any thing you supply as an input to a file and you get arbitrary file writing!
Now here’s where knowing the OS and server software come into play. Having an arbitrary file writing on a system that you know nothing about isn’t much fun (unless you sprinkle some brute forcing on top).
My main goal was to leverage a “Living off Land” strategy. So since this is a windows machine with a xampp server on it, we know that the root directory from which everything is served is at C:\xampp\htdocs\, and since the P in XAMPP stands for PHP, we can utilize that to execute commands on the system without introducing any new binaries to the file system or making the SQL server bend over backwards to execute commands for us using something like raptor_udf etc…
That said, the final query will look like that:
If the query completes, and nothing like secure-file-priv ruins our party, we should find our shell at https://www.legitsite.com/xampp/plsdontdelete.php
And would you look at that:
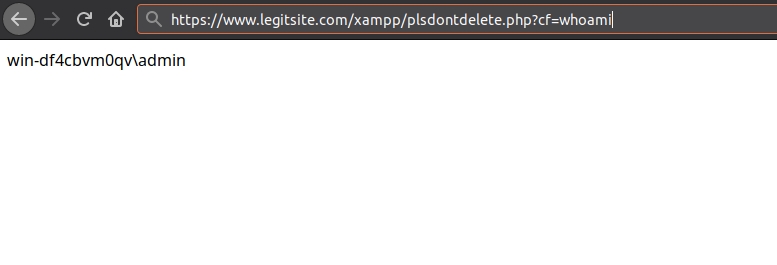
Stay tuned for part II where we will explore the guts of the server and all the fun things that were done with it.
Disclaimer: This story & the techniques mentioned therein are for educational purposes ONLY and does not necessarily reflect an actual event that took place in the real world.
Last updated